Hi,
There was an opportunity like a blind chicken grain long ago and I hunted the domain for free sysadmin.info.pl. Originally the idea was to use it for engineering work and so it happened. Three months later again an opportunity came up, which I couldn’t miss. This time the virtual machine on OpenVZ for funny money. If you are interested, please contact https://mikr.us . After clicking on the link you will get a 5% discount on the server for the year
This way it became possible to have a live version of your own website, the configuration of which I will describe below step by step. By the way I will show you how to protect everything and prove that the default configuration of 128 MB RAM and 128 MB swap is enough to have a website based on and so popular WordPress CMS, which is the most frequently attacked CMS in the world. But about this maybe in a different entry. Hardening Linux was the subject of my engineering work, so by the way I will share a few comments on this subject, as well as show what on mikr.us can and can not do.
I asked to change the default Ubuntu 16:04 to CentOS 7 and got version 7.6. Revelation, I like it. After some minor problems I finally managed to bring my website back to life and at the same time refresh my knowledge of building a web server on CentOS. So here we go. Little edit: now you can choose what operating system you want to use. Just ask for it through e-mail address which can be found on https://mikr.us website.
Create an account on cloudflare.com and set up a domain
Create a free basic account on https://www.cloudflare.com/
Confirm your email and go to domain configuration where you have a panel from your domain. Change the DNS servers (ns1 and ns2) there to:
|
|
Log in to cloudflare. Add domain.
Set AAAA record as a domain name and as an IPv6 IPv6 address. You will find this address by entering a command in the terminal:
|
|
It will be given in this form: 2001: ….
Copy it for yourself or write it down without the last elements: /128
Paste it into the content field. Save the change.
Click on the SSL/TLS icon and set it as shown in the picture below:
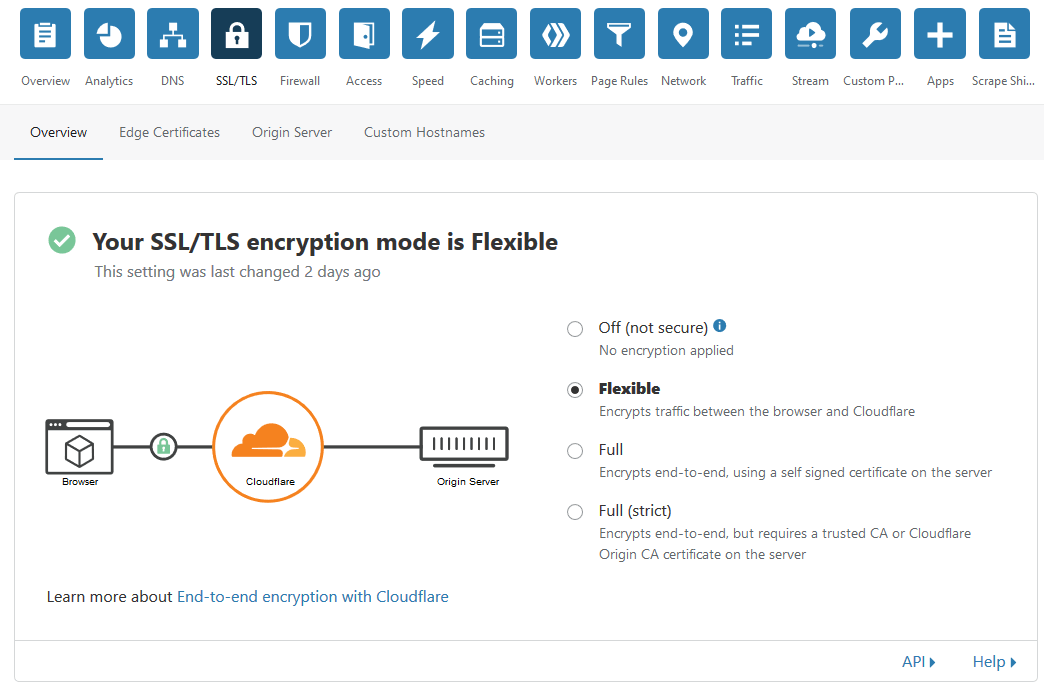
Click on Edge Certificates and set it up:
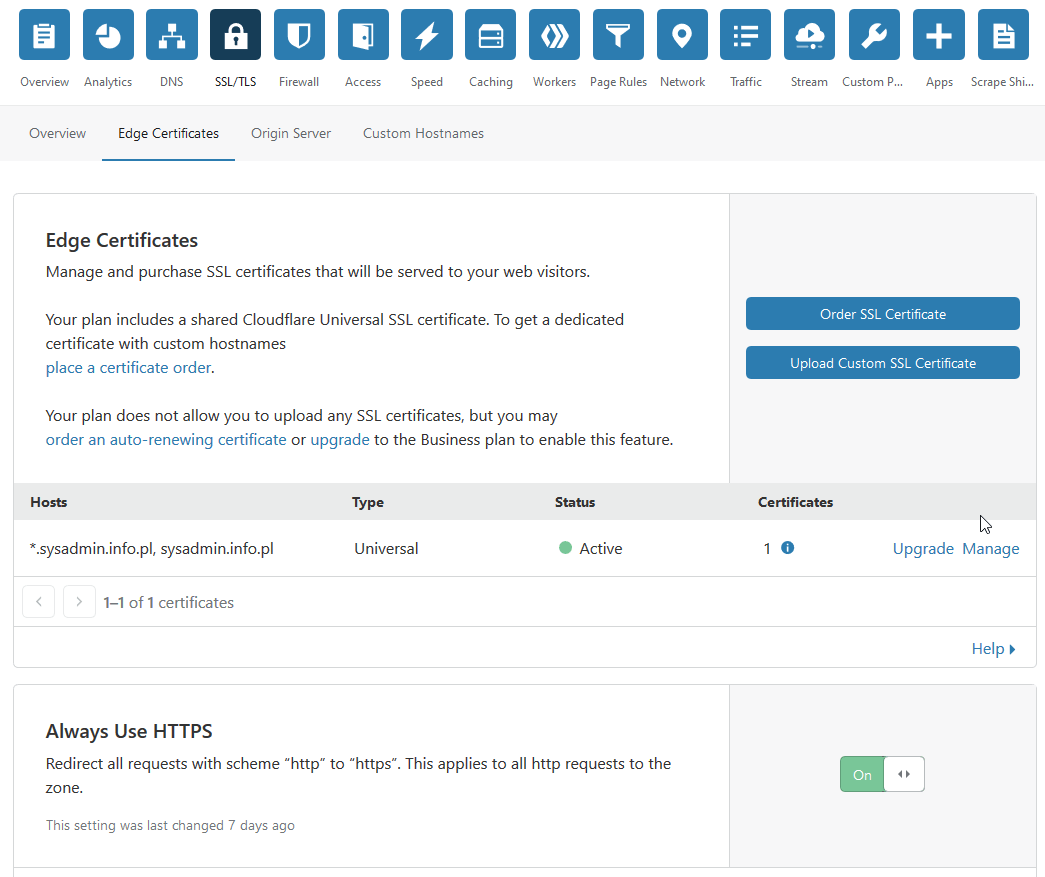
Below are the options that should be enabled:
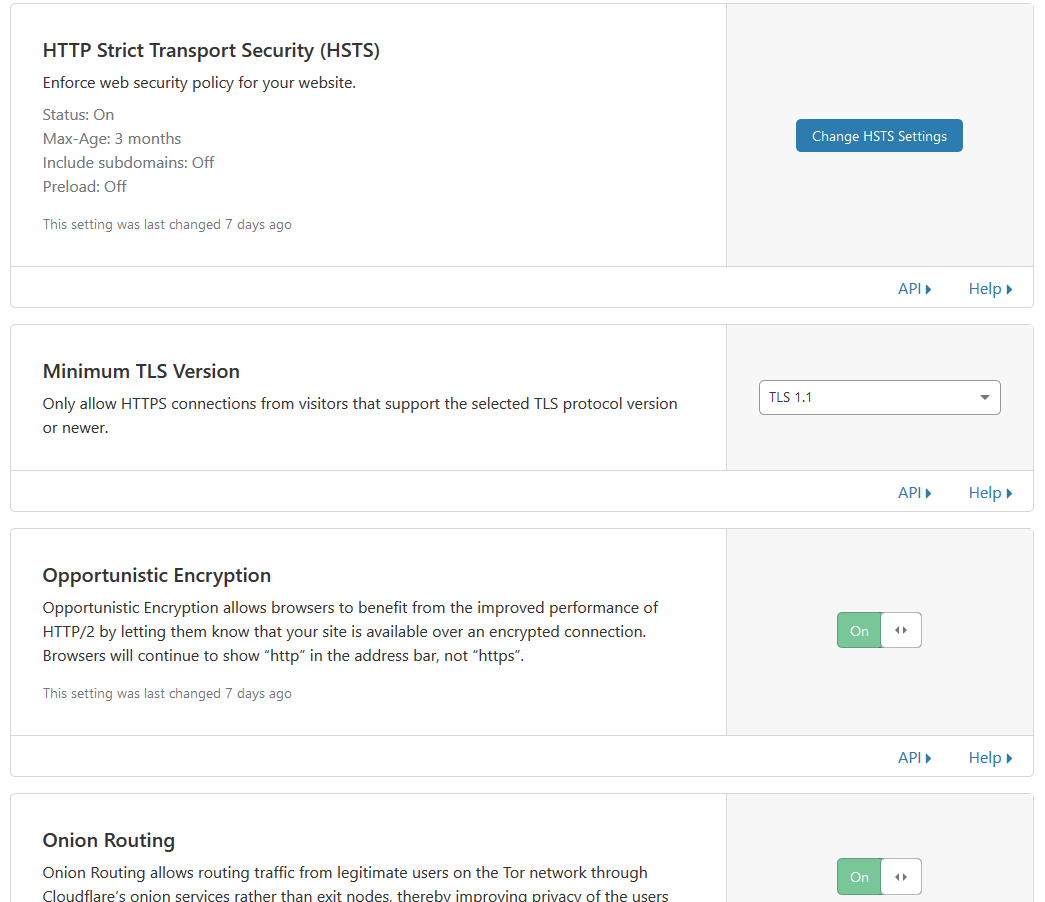
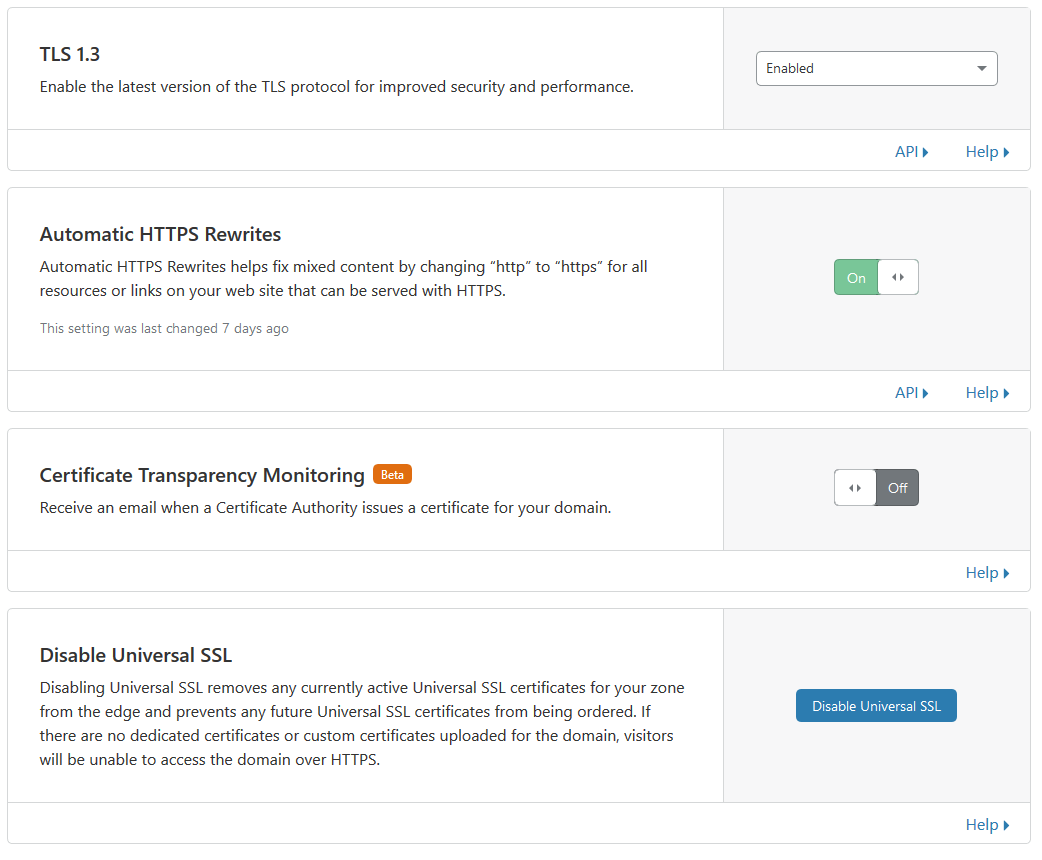
Then click on Page Rules and add the rule by clicking on Create Page Rule.
Domain name on e.g.
http://example.com.pl
(remember about http not https).
Select Automatic HTTPS rewrites from the drop-down list and set to ON.
Click save and deploy.
If you have any questions about other settings, please write in your comment what bothers you.
Login to ssh and its hardening.
Access to the virtual machine is only possible after ssh.
First you need to change your root password for security reasons, because you get a temporary password to login, server address and you can use only root account for the first login, which is not safe in itself.
|
|
Once the password is set, we need to add a user to be used to log in to ssh and replace it with root for security reasons, but to be able to execute commands with root rights sometimes, we will add the user to the sudoers group.
|
|
Next, block root user for ssh connections. To do this, you need to edit the sshd_config file.
|
|
We find the entry and set it this way: PermitRootLogin no To edit, press insert, change the value from yes to no. Next, press Esc, type :wq and press Enter. This is how we saved the changes. Now there is still a restart of the ssh daemon.
|
|
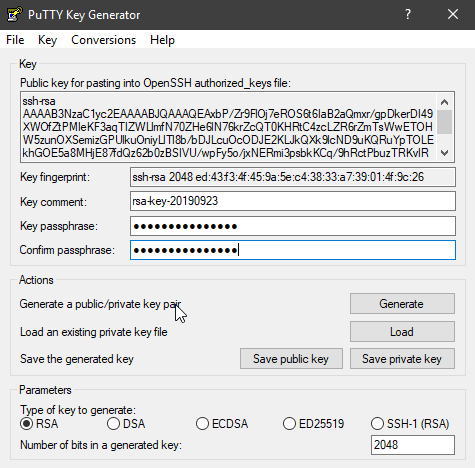
I assume that everyone knows how to connect to the server using a terminal or putty. Below I will describe two methods of generating a pair of keys (private and public) both in putty and in terminal. Open PuTTYgen.exe, press the Generate button, move the mouse to randomly generate a key pair using the RSA algorithm. After generating the keys, type in a password (passphrase) (select „hard to guess”). Save the public key. Save your private key. 2048 bits is enough, but if you want to increase the security level, you can set 4096 bits in the window.
After logging in with ssh and your user account, in our case it will be a user, follow the instructions below.
|
|
Copy from the field from ssh-rsa to the end of everything, go to the logged-in session, press the insert, paste the whole thing with the right mouse, then press Esc, type :wq and press Enter. Then set the file to read only with the command:
|
|
|
|
Next, edit the /etc/ssh/sshd_config file, as above. Change the values to: RSAAuthentication yes and PubkeyAuthentication yes, as well as PermitEmptyPasswords no and PasswordAuthentication no. Save the file as described above. (I assume that using vi has already been understood). Restart ssh with a command:
|
|
In connection with the putty or terminal we have to indicate the private key file for authorization. Or in the case of putty, double-click the private file, enter the password and the program pageant.exe should load the private key into the memory. If we don’t have a pageant, the server will ask us for the password for the private key (passphrase) that was set after the key was generated (this increases the security level, because even if someone manages to capture the key, they don’t know the password).
If you are using a terminal, you generate a command to generate a key on your computer from the terminal level:
|
|
Then you copy the key to the server with a command:
|
|
You change the port number 12345 to the one you received in the email, and the name is the same as the port number. I described above how to block access to ssh for root user. Now all you need to do is restart ssh daemon.
|
|
Hang up the exit command and connect again using ssh root@root@name.mikr.us -p 12345.
The security level can be further increased by adding a group to the ssh login and adding a user to this group.
|
|
Wyświetli się: user : user sudo grupassh lub user : user wheel grupassh
|
|
Dodaj: AllowGroups grupassh
|
|
For the safety of Ubuntu/Debian users I recommend to install policies.
|
|
They specify the length of the password, how many times the user can log in, how many times the same characters can be used in the password, the complexity of the password, its strength, number of digits, lowercase, uppercase letters and special characters.
Web/www server installation with Apache
First clear the download manager. CentOS uses yum, while Debian/Ubuntu uses apt-get and in the newer distro apt.
CentOS section
|
|
Ubuntu section
|
|
Install all updates:
CentOS section
|
|
Ubuntu section
|
|
Next, install Apache (httpd in CentOS, apache2 in Debian/Ubuntu).
CentOS section
|
|
Ubuntu section
|
|
Enable Apache at system startup and run the service.
CentOS section
|
|
Ubuntu section
|
|
You can check the status of the service:
CentOS section
|
|
Ubuntu section
|
|
Virtual host configuration
In the case of CentOS we create a virtual host file for http (port 80) using the following command:
|
|
In the case of Ubuntu
|
|
|
|
For Debian/Apache we still have to turn on the page.
|
|
This will create a symbolic link in the /etc/apache2/sites-enabled directory.
Create a physical structure and upload WordPress to the server.
Now you need to create a directory for the page in /var/www/html directory.
|
|
(enter the password of the user you created at the beginning)
|
|
Create a directory named src in your site directory to store new copies of WordPress source files. This guide uses the home directory /var/www/html/example.com.pl/ as an example. Go to this new directory:
|
|
Set the web server user, www-data, as the owner of the home directory of your site. www-data is a group. In the case of CentOS it will be an apache group.
CentOS section
|
|
Ubuntu section
|
|
Install the latest version of WordPress and extract it using the appropriate name depending on the system you are using:
|
|
Rename the latest.tar.gz file to wordpress, then set the backup date for the original source files. This will be useful if you install new versions in the future and need to return to the previous version:
|
|
Create the public_html directory, which will be the WordPress root directory. Move the WordPress files to the public_html folder:
|
|
Give the public_html folder permissions for the www-data or apache group:
CentOS section
|
|
Ubuntu section
|
|
Go to the directory where WordPress was extracted, copy the sample configuration and set it to use the remote database:
|
|
Change the login variables to match the database and the user. Edit the file:
|
|
Add security keys to protect wp-admin.
Use Security Key Generator WordPress to create random, complex hashes that WordPress will use to encrypt your login data. Copy the result and replace the corresponding section in the file wp-config.php:
|
|
Installation and configuration of Maria DB 10.4 in CentOS 7.6.
|
|
|
|
When configuring, confirm the empty root password in MariaDB, and in the next step set the root password (the one from MariaDB). This password should be different from the root password you got in the email after setting up the server on mikr.us.
|
|
|
|
|
|
After logging in to the database, create a database and assign it to the user.
|
|
Enter
|
|
enter the password of the user you just created
|
|
If it shows the MariaDB version, everything is working.
|
|
Enter
Restart the database server and web commands:
|
|
Installation and configuration of Maria DB 10.3 in Ubuntu/Debian
To install MariaDB 10.3 on Ubuntu 16.04, you need to add the MariaDB repository to your system. Run the following commands to import the PGP key of the MariaDB repository and add the repository.
|
|
Update the list of system packages and install MariaDB.
|
|
You will be asked to enter the password of the MariaDB root. You will have to enter it twice. Confirm the change of password. You can confirm the installed version of MariaDB by logging in as root user.
|
|
After logging in, enter the status; (remember about semicolons in SQL syntax). Then type exit.
I recommend performing exactly the same procedure as for CentOS installation. Above you can see what steps need to be taken.
|
|
Then follow the instructions from CentOS installation:
|
|
Create a user database in the same way as creating a database in CentOS.
Installation and configuration of SSL certificate using Let’s Encrypt.
We will use the https://certbot.eff.org website to do this.
From the Software drop-down list, select Apache, the operating system, either Ubuntu 16.04, Debian 9, or CentOS/RHEL 7 and follow the instructions.
Choose a web page without a www or with a www as you like, because certbot will recognize the virtual host for http that was created earlier.
Do not enable redirection from http to https, as you will do so on the Cloudflare side. Otherwise you will encounter an error. So choose 1 when it asks for redirect.
Certbot will automatically install the certificate, create a virtual host file. Now all you have to do is go to the directory:
|
|
I recommend to modify the virtual host file for https to make it look like this:
CentOS section
|
|
Ubuntu section
|
|
|
|
Configuration of MyISAM engine in MariaDB instead of InnoDB.
CentOS 7.6 section
In CentOS we edit the my.cnf file.
|
|
Now basically it is enough to replace this file with what is shown below:
|
|
Save changes, restart httpd and mariadb.
|
|
Ubuntu
In the case of Ubuntu 16.04, the location of the file is slightly different.
|
|
Just paste into this file what is in the [mysqld] section above. However, I recommend that you enable error logging to mariadb and set the error logging in my.cnf, as above it is visible.
|
|
Save changes, restart apache2 and mariadb.
|
|
PHP 7.3 installation
CentOS
PHP 7.3 installation – CentOS 7.6
The assumption is that there is a user added to the wheel group (sudoers) at the very beginning of the tutorial. After sudo -i the user password is given, not root.
|
|
Debian/Ubuntu
PHP 7.3 installation – Ubuntu 16.04
|
|
Setting the memory limit in PHP
|
|
CentOS 7.6 section
|
|
Ubuntu 16.04 section
|
|
Set:
|
|
Apache optimization
CentOS
|
|
Debian/Ubuntu
|
|
Add this at the end of this file:
|
|
Save the file and exit.
Installation and configuration of iptables
CentOS
Installation and configuration of iptables in CentOS 7.6
Turn off the firewalld:
|
|
Install iptables and turn it on.
|
|
Check the status of the iptables and the rules.
|
|
Add rules for iptables.
|
|
Save changes.
|
|
Debian/Ubuntu
Installation and configuration of iptables in Ubuntu 16.04
|
|
During installation, it will ask you whether you want to keep the current rules and whether you want to use both IPv4 and IPv6. All these questions will be answered in the affirmative.
|
|
Add ports.
|
|
Save changes and reload the service:
|
|
Now go to https://example.com.pl and install WordPress.
I recommend installing Cloudflare plug-in and integrating it with the service after the installation.